Demystifying XMAC: Expected Message Authentication Code
telcomatraining.com – In the realm of data security, the need for robust and efficient mechanisms to ensure the integrity and authenticity of transmitted messages is paramount. Among the various methods employed for message authentication, XMAC, or Expected Message Authentication Code, stands out as a promising technique. This article delves deep into what XMAC is, how it functions, and its importance in modern cryptography.
What is XMAC?
XMAC (Expected Message Authentication Code) is a cryptographic algorithm designed to ensure the integrity and authenticity of messages in a communication system. It’s an advanced version of traditional message authentication codes (MACs), offering enhanced security features that are specifically beneficial in environments where both speed and reliability are critical.
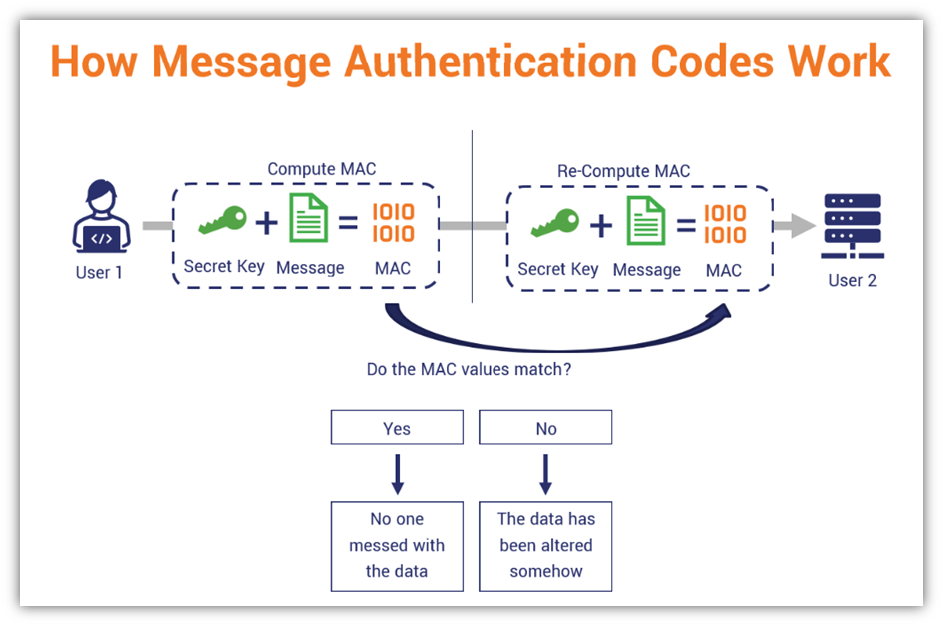
At its core, XMAC is used to verify that the message received by a recipient has not been altered in transit and that the message genuinely comes from the claimed sender. Unlike traditional MACs, which rely on fixed secrets to generate and verify tags, XMAC uses an expected value derived from a specific protocol or system to generate the authentication code. This design significantly reduces the computational overhead while maintaining high security.
How Does XMAC Work?
XMAC functions by appending a short code to the message, called the “authentication tag,” which is created by applying a cryptographic algorithm using a secret key and an input message. However, what sets XMAC apart is its innovative approach in generating the authentication tag. It leverages an expected message model, where the sender and receiver are both aligned on the structure and expectations of the message content. This pre-shared expectation enables the algorithm to more efficiently validate the authenticity of the message.
The key steps involved in the XMAC process include:
- Key Generation: Both the sender and receiver generate a shared secret key, used to secure the authentication tag.
- Message Input: The sender inputs the message that is to be transmitted, ensuring it follows the expected message format that both parties agree upon.
- Tag Creation: XMAC generates an authentication tag by processing the message and key through a cryptographic function that produces a unique output.
- Message Transmission: The message along with the authentication tag is transmitted to the recipient.
- Tag Verification: Upon receiving the message, the recipient uses the same expected message model and shared key to verify that the tag matches the message. If the values align, the message is authentic and intact.
Advantages of XMAC
XMAC presents several key benefits over traditional message authentication codes:
- Efficiency: Since XMAC leverages an expected message model, it reduces the complexity of traditional MAC schemes. This makes it a highly efficient solution for systems with limited computational resources.
- Enhanced Security: XMAC’s reliance on a shared expectation between the sender and receiver strengthens its resilience against certain types of attacks, such as replay and tampering attacks.
- Scalability: The expected message model of XMAC is adaptable to different kinds of applications, making it suitable for a wide variety of cryptographic use cases, from secure messaging to financial transactions.
- Reduced Overhead: By utilizing the concept of expected messages, XMAC eliminates the need for excessive computations, reducing overall processing time and resource consumption.
Real-World Applications of XMAC
XMAC is particularly valuable in real-time systems, where low-latency communication is crucial. Some of the domains where XMAC has proven to be beneficial include:
- Wireless Communications: In scenarios where messages are sent over unstable channels, ensuring that the message is not tampered with or altered is critical. XMAC provides an efficient mechanism for message authentication without introducing significant delays.
- Internet of Things (IoT): The growing number of IoT devices demands authentication methods that are lightweight and energy-efficient. XMAC’s low overhead makes it an ideal candidate for securing IoT communications.
- Secure Messaging Applications: XMAC ensures that messages sent over messaging platforms remain unaltered and are from trusted senders, crucial for maintaining user privacy and data integrity.
- Blockchain Technology: In blockchain networks, where transaction integrity is paramount, XMAC can help secure communication between nodes and ensure that messages exchanged across the network are valid.
Conclusion
XMAC represents a significant advancement in the field of cryptography, providing an efficient and secure way to authenticate messages. Its reliance on expected message models makes it a powerful tool for reducing overhead while maintaining a high level of security, making it ideal for a variety of modern applications. As the demand for secure communication in both traditional and emerging technologies grows, XMAC stands poised to play an essential role in shaping the future of cryptographic security.