What Is NGKSI (Key Set Identifier) for 5G?
What Is NGKSI (Key Set Identifier) for 5G?
1 | Overview
Every secure 5G session begins with a security context—a bundle of cryptographic keys and counters shared by the user equipment (UE) and the 5G core. The New-Generation Key Set Identifier (ngKSI) is the compact label that tells both sides which security context they are talking about, so that subsequent NAS (Non-Access Stratum) signalling can be protected without ambiguity. Think of it as the “folder name” that points to the right set of keys inside the UE and the Access & Mobility Management Function (AMF).
2 | Formal Definition
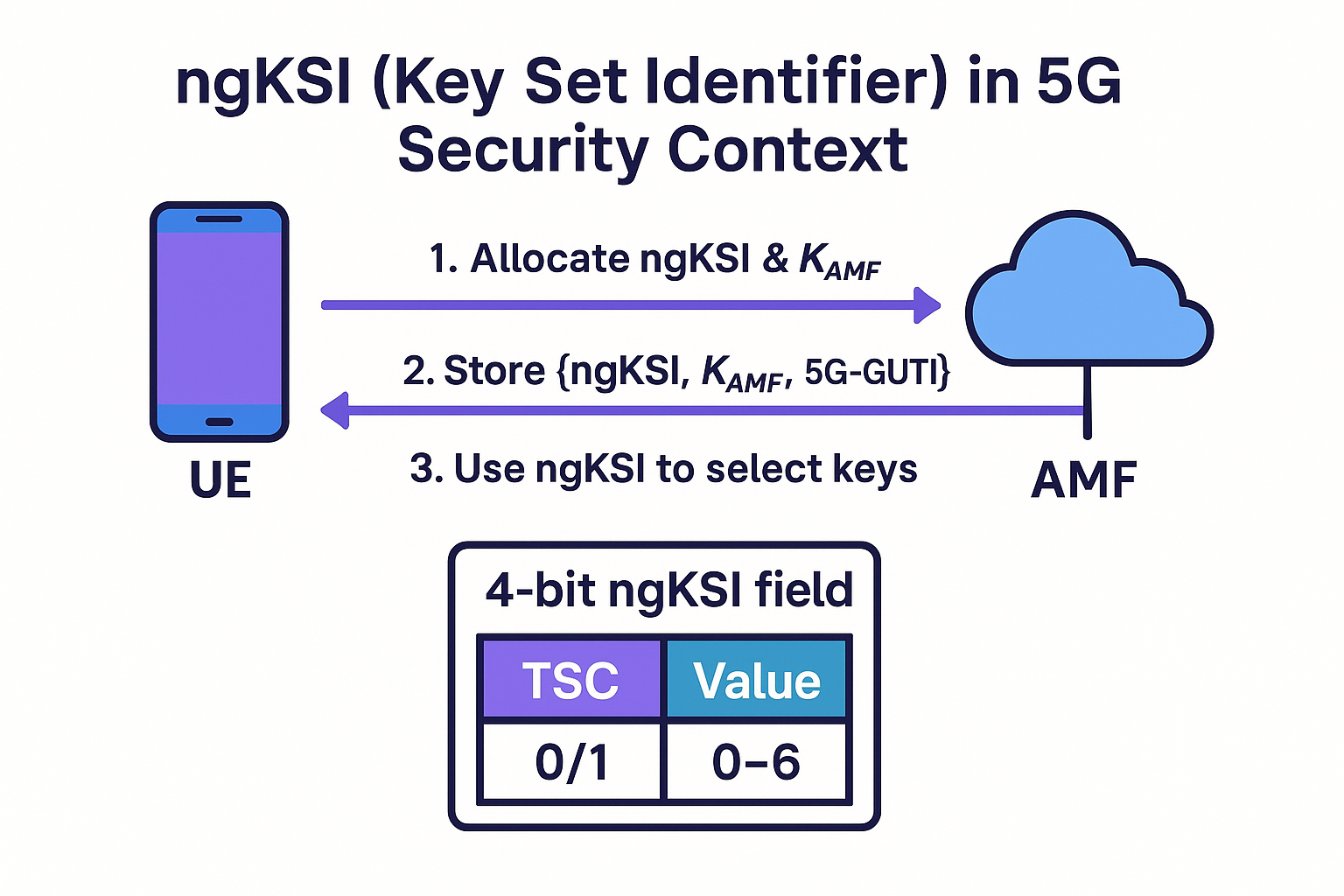
In 3GPP TS 33.501, ngKSI is defined as “the key-set identifier that accompanies K<sub>AMF</sub> and allows the UE and AMF to retrieve the same NAS security context.” It replaces the LTE-era KSI<sub>ASME</sub> and is mandatory for all 5G devices. The parameter is stored alongside K<sub>AMF</sub> in both the UE and AMF databases.
3 | Structure & Encoding
| Field | Bits | Purpose | Typical Values |
|---|---|---|---|
| TSC (Type of Security Context) | 1 | Distinguishes native (0) from mapped (1) contexts | 0 = native, 1 = mapped |
| Value | 3 | Index to one of up to seven parallel key sets | 000–110 (111 is reserved) |
A complete ngKSI is therefore 4 bits long and fits neatly inside NAS messages such as Registration Request or Security Mode Command.
4 | Native vs Mapped Contexts
| Context Type | How It Is Created | When It Is Used |
|---|---|---|
| Native | Generated during primary authentication between UE and SEAF; SEAF allocates the ngKSI. | Pure-5G sessions on NR or non-3GPP access. |
| Mapped | Derived from existing LTE EPS keys during EPS-5G inter-working. | Idle-to-connected transitions where the UE roams from LTE to 5G (or vice-versa). |
The TSC bit inside ngKSI lets the UE instantly know whether it should look for a 5G-native K<sub>AMF</sub> or dig into its cache of mapped contexts that originated from LTE keys.
5 | Lifecycle of an ngKSI
- Allocation – During primary authentication the SEAF selects an unused 3-bit value and returns it with the Authentication Request.
- Storage – UE and AMF save {ngKSI, K<sub>AMF</sub>, 5G-GUTI}.
- Usage – Subsequent NAS messages carry the ngKSI so both sides pick the correct encryption (K<sub>NASenc</sub>) and integrity (K<sub>NASint</sub>) keys without running a fresh AKA.
- Refresh & Re-key – If the AMF detects replay risk or key expiry it issues a new ngKSI in a Security Mode Command; the old identifier becomes “non-current.”
- Release – Contexts tied to an ngKSI are deleted after timer expiry, explicit Deregistration, or inter-PLMN hand-over.
A special NAS cause value #71 “ngKSI already in use” exists for conflict handling when the network tries to allocate an ngKSI that the UE still marks as active.
6 | Why Does ngKSI Matter?
| Benefit | Explanation |
|---|---|
| Fast Resume | Lets a UE resume secure signalling in milliseconds by pointing to an existing key set instead of re-authenticating. |
| Roaming Efficiency | During inter-system mobility (LTE ⇄ 5G) the mapped/native flag prevents key mismatches that could drop calls. |
| Replay Protection | A fresh ngKSI value signals that counters have reset, stopping attackers from replaying old NAS messages. |
| Slice-Aware Security | Because 5G lets one UE hold multiple security contexts (one per AMF or network slice), the 3-bit value field provides up to seven parallel key labels. |
| Troubleshooting Simplicity | Operators can correlate logs by ngKSI to trace exactly which key set caused an integrity-check failure. |
7 | Common Implementation Pitfalls
- Exhausting the 3-bit pool in IoT-dense cells—use shorter context timers or forced re-authentication when the pool is close to saturation.
- Mismatched Context Type when transitioning between EPS and 5GS—ensure the UE clears stale mapped contexts on EPS detach.
- NAS Cause #71 Loops—older firmware may keep sending Registration Requests with an ngKSI the network has already retired; a software patch is usually required.
8 | Looking Ahead
Nothing in Release 17/18 changes the format of ngKSI, but emerging features such as 5G Non-Terrestrial Networks and Edge Multi-AMF make its correct handling even more critical—UEs may juggle multiple AMFs across satellite and terrestrial links, each with its own ngKSI.
9 | Key Takeaways
- ngKSI is a 4-bit pointer that ties NAS messages to the right K<sub>AMF</sub>.
- The TSC bit flags native vs mapped contexts, easing LTE–5G mobility.
- Proper lifecycle management of ngKSI keeps 5G sessions fast, secure, and resilient against replay or key-mixing attacks.
In short, ngKSI is the tiny identifier that guarantees the giant 5G security stack knows exactly which keys to use—without it, all the cryptography in the world can’t keep your connection safe.