Understanding Lawful Interception (LI) in 5G Networks: Security and Compliance Explained
telcomatraining.com – As mobile networks continue evolving, the introduction of 5G has brought unparalleled speed, connectivity, and complexity. While these advancements benefit consumers and businesses, they also raise new security challenges. One critical element for maintaining lawful order and national security is Lawful Interception (LI)—a legal process allowing authorized entities to monitor communications. This article explores how lawful interception functions within 5G networks, why it matters, and how it aligns with global compliance standards.
What is Lawful Interception?
Lawful Interception is the legally sanctioned access to private communications, such as phone calls, SMS, emails, and internet traffic, by law enforcement or intelligence agencies. It’s typically executed under the framework of national laws and requires court orders or legal mandates. The goal is to detect, prevent, or investigate serious crimes and threats, such as terrorism, drug trafficking, and cybercrime.
Why is LI More Complex in 5G?
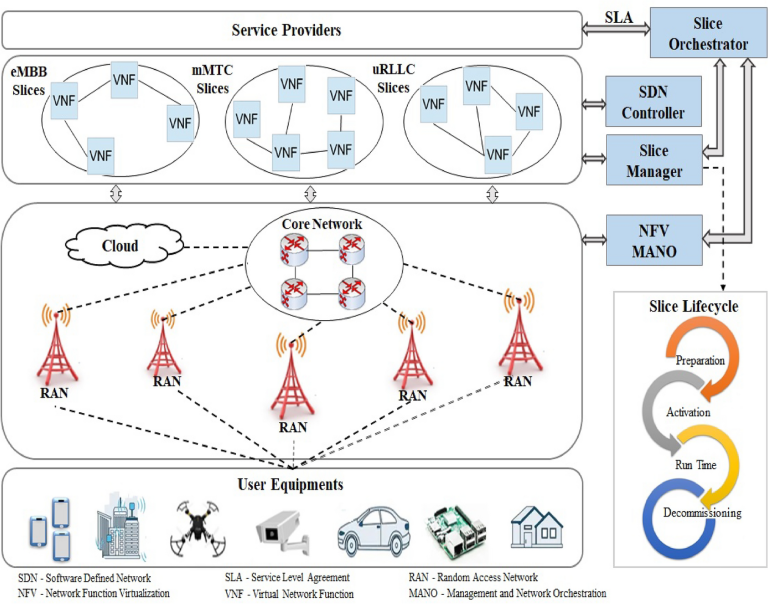
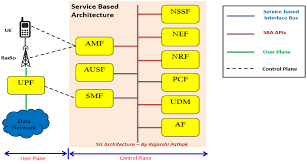
5G introduces a new set of technical and architectural challenges for implementing lawful interception. Unlike previous generations, 5G is designed with a service-based architecture (SBA), virtualization, edge computing, and network slicing. These features create a decentralized and highly dynamic network environment, making it harder to identify and monitor specific targets.
For example, in 5G, a user’s data may be processed across multiple virtual machines in different locations. Network slicing allows different services (e.g., autonomous vehicles, IoT, or telemedicine) to operate independently on the same physical infrastructure. Therefore, interception must be integrated at multiple layers without disrupting service quality or user privacy.
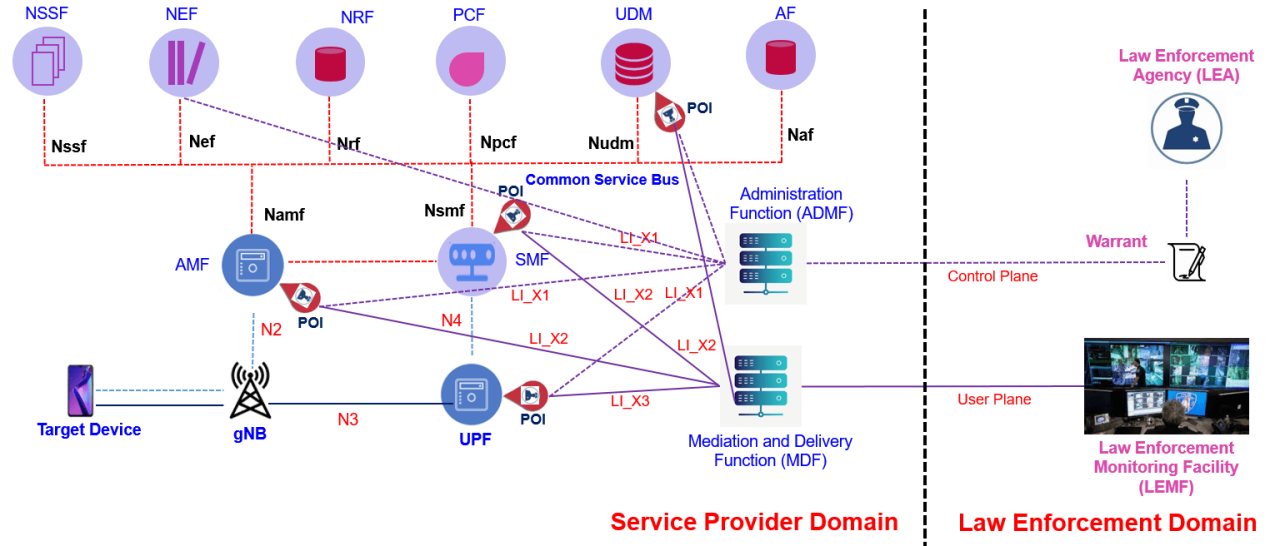
Key Components of LI in 5G
To ensure effective and compliant interception in 5G networks, certain technical standards and interfaces must be implemented:
- HI1 (Administrative Interface): Used for receiving interception orders.
- HI2 (Content of Communication Interface): Transfers the actual content, such as voice or data.
- HI3 (Intercept Related Information): Provides metadata, like call duration, location, and session details.
These interfaces must adhere to international standards such as those from the ETSI (European Telecommunications Standards Institute) and comply with legal frameworks like the GDPR, CALEA (U.S.), or other regional laws.
Legal and Ethical Considerations
While lawful interception is vital for national security, it must strike a careful balance with individual privacy rights. The implementation must follow due legal process and maintain transparency and accountability. Unauthorized interception or lack of safeguards can lead to legal challenges, data breaches, and loss of public trust.
Therefore, telecom operators are legally required to:
- Ensure interception capabilities are embedded in their infrastructure.
- Keep interception systems tamper-proof and confidential.
- Cooperate with government agencies under legal requests.
Failure to comply may result in heavy penalties or loss of operating licenses.
Challenges Ahead
Implementing lawful interception in 5G networks comes with several challenges:
- Encryption and End-to-End Security: Many services use strong encryption, making it difficult to intercept data even with legal approval.
- Cross-Border Data Flows: 5G enables global data distribution, raising jurisdictional issues when intercepting communications across borders.
- Data Volume and Speed: The sheer volume and velocity of 5G data traffic require robust, real-time processing capabilities.
To address these, operators must invest in modern interception solutions that support high scalability, automation, and compliance auditing.
Conclusion
Lawful interception in 5G networks is not just a technical necessity but a legal and ethical imperative. It plays a crucial role in safeguarding public safety while ensuring compliance with national and international regulations. As 5G continues to roll out, stakeholders—from network providers to regulators—must collaborate to develop secure, transparent, and compliant LI frameworks that protect both public interest and individual rights.