Simplifying Network Complexity with NFV: A High-Level Architectural Overview
telcomatraining.com – In today’s rapidly evolving digital landscape, service providers are under constant pressure to deliver faster, more agile, and cost-efficient network services. Traditional hardware-based network infrastructures, while reliable, often struggle to keep up with the demands of scalability, flexibility, and innovation. This is where Network Functions Virtualization (NFV) comes in—offering a software-based approach to simplify and optimize modern network architectures.
What is Network Functions Virtualization (NFV)?
Network Functions Virtualization (NFV) refers to the concept of decoupling network functions—such as firewalls, load balancers, and intrusion detection systems—from proprietary hardware appliances and running them as software on standard servers. This approach drastically reduces the reliance on specialized hardware, enabling service providers to deploy and manage network services dynamically and cost-effectively.
NFV leverages the principles of virtualization widely used in cloud computing. It allows multiple virtual network functions (VNFs) to run on shared hardware resources, promoting better utilization and simplified management.
The Need to Simplify Network Complexity
Legacy networks often rely on fixed-function devices, each requiring specific configurations, updates, and maintenance. As the number of connected devices and user demands grow, these hardware-centric models become difficult to scale, manage, and secure.
NFV addresses this complexity by transforming how networks are built and operated. It enables centralized orchestration, automated service deployment, and faster time-to-market for new offerings. As a result, service providers can better handle growing traffic, diverse applications, and ever-changing user expectations.
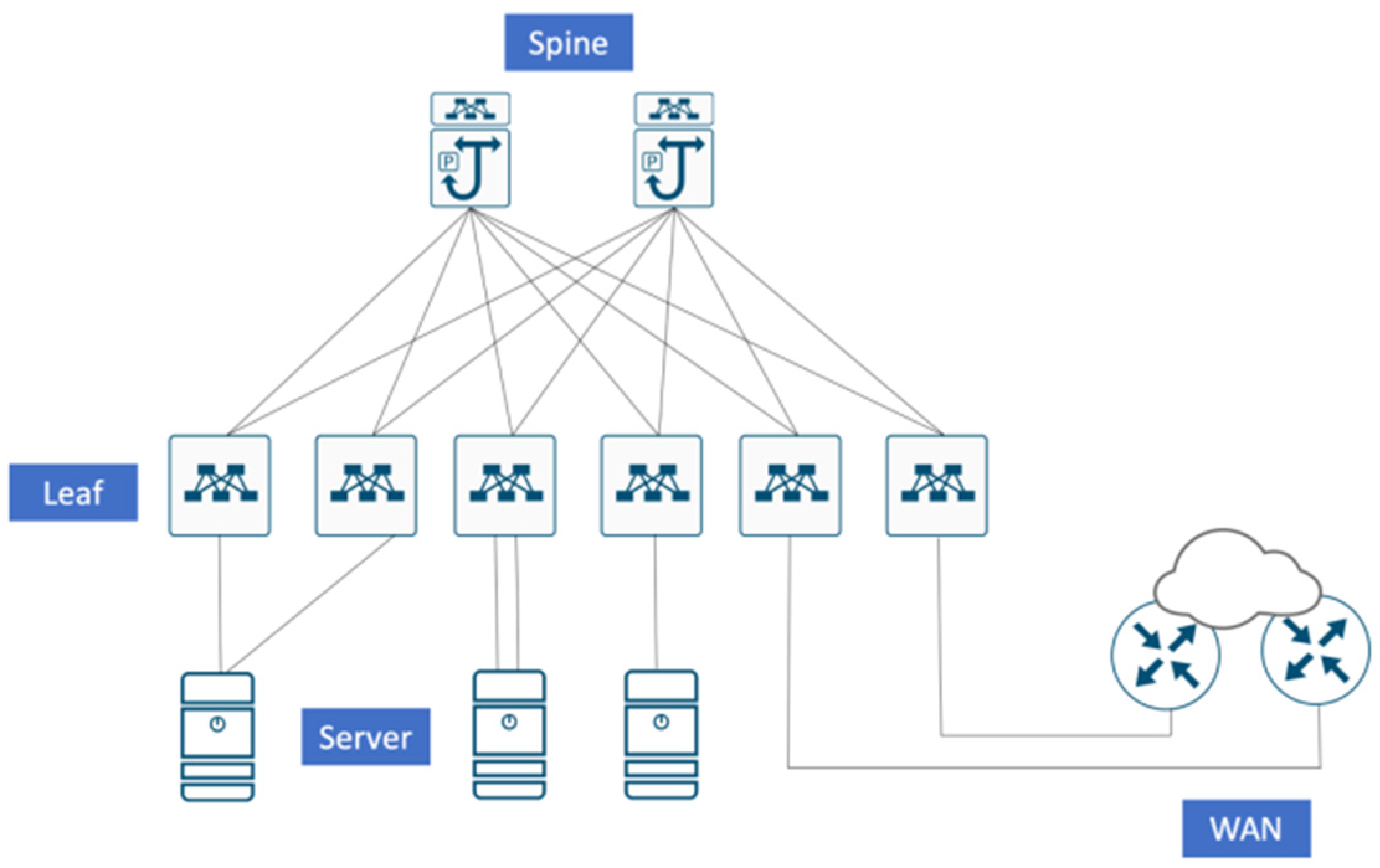
High-Level NFV Architecture Overview
The NFV architecture is designed around a few key components that work together to deliver network services in a flexible and scalable manner:
1. Virtual Network Functions (VNFs)
VNFs are the software implementations of individual network functions that traditionally run on hardware. Examples include virtual firewalls, routers, and session border controllers. These VNFs can be instantiated and terminated as needed, enabling agile service delivery.
2. NFV Infrastructure (NFVI)
NFVI comprises all the hardware and software resources that provide the environment in which VNFs operate. This includes computing, storage, and networking components, typically built on commercial off-the-shelf (COTS) hardware. Virtualization layers, such as hypervisors or container platforms, are also part of the NFVI.
3. NFV Management and Orchestration (MANO)
The MANO framework is crucial for managing and orchestrating VNFs and the underlying infrastructure. It includes:
- Orchestrator: Coordinates the overall lifecycle of network services.
- VNF Manager: Handles the lifecycle of individual VNFs.
- Virtualized Infrastructure Manager (VIM): Manages compute, storage, and network resources.
MANO ensures that the system operates smoothly by automating deployment, scaling, healing, and monitoring tasks.
Benefits of NFV in Network Simplification
NFV offers multiple advantages that directly contribute to simplifying network complexity:
- Operational Efficiency: Automating routine tasks reduces manual intervention, streamlining network operations.
- Scalability: NFV allows dynamic scaling of network resources based on demand, eliminating overprovisioning.
- Cost Reduction: Running VNFs on standard hardware lowers capital and operational expenses.
- Flexibility: Rapid deployment of new services without the need for new hardware accelerates innovation.
- Improved Resilience: Centralized control and orchestration enable faster response to failures and better fault management.
Real-World Applications of NFV
Major telecom operators and enterprises are increasingly adopting NFV to modernize their infrastructure. Examples include virtualized Customer Premises Equipment (vCPE), mobile core networks (vEPC), and cloud-based security services. NFV also supports 5G networks by enabling network slicing and edge computing capabilities.
Conclusion
NFV is transforming how network services are delivered, managed, and scaled. By virtualizing network functions and automating their orchestration, NFV reduces complexity, enhances flexibility, and drives cost-efficiency. As digital transformation continues to accelerate, embracing NFV becomes a strategic imperative for organizations aiming to stay competitive in the era of cloud-native networking.